mDocs remote web verification journey pattern
This journey pattern is used to verify an mDoc remotely via an online verification workflow, as per ISO/IEC 18013-7:2025 and OID4VP.
Overview
- Issuance channel: Remote, unsupervised
- Device/s: Same-device / Cross-device
- Formats: mDocs
- Information assurance level: High
- Identity assurance level: High
Journey flow - Same-device

Accessing the service
Samantha opens a web application in her mobile browser. She begins an interaction that requires her to verify her identity.
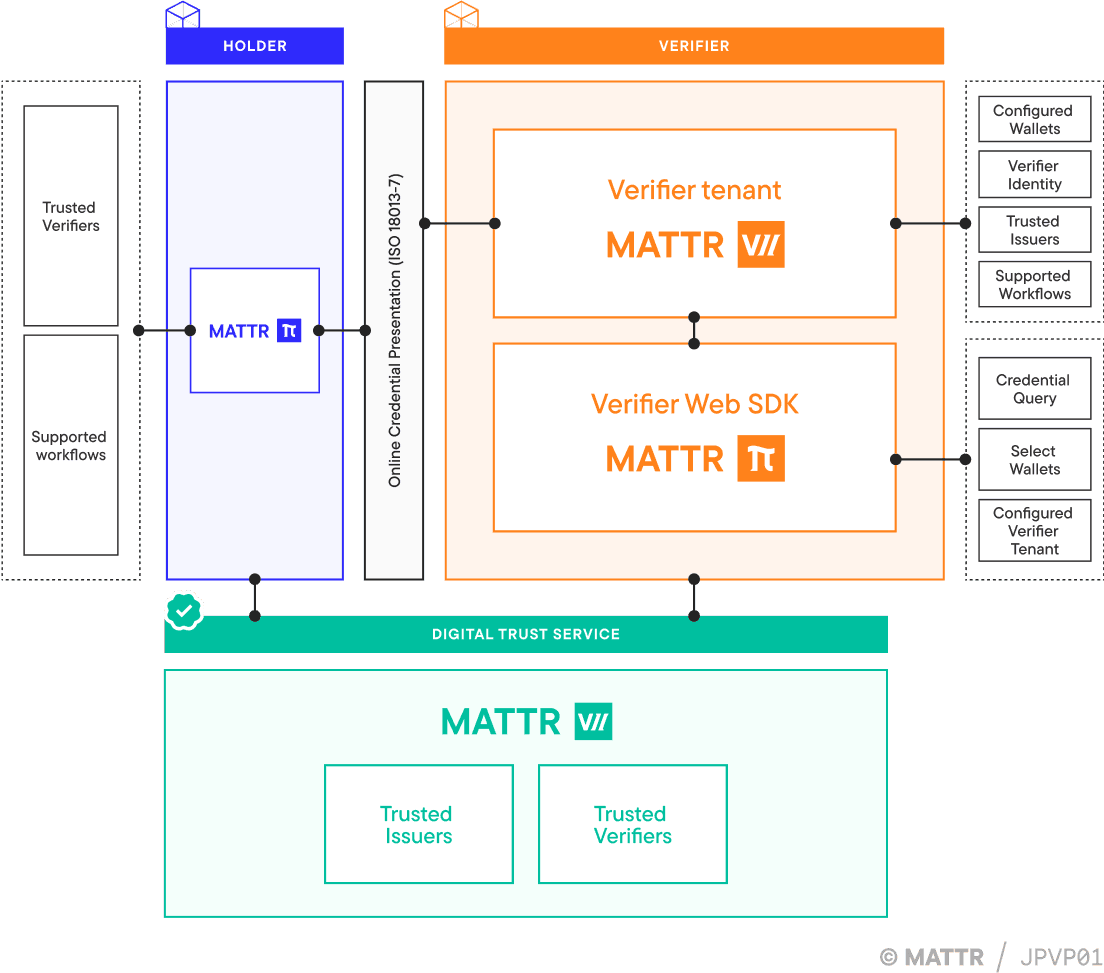
Architecture - Same-device
Interacting with the website
The user accesses a website using a mobile browser on the same device that holds their wallet app.
Requesting a credential for verification
On the website, the user begins an interaction that requires them to present a credential.
The MATTR Pi Verifier Web SDK, embedded in the web application, initiates the verification request by sending it to a configured MATTR VII verifier tenant. This request defines:
- The credentials and claims required
- The supported interaction modes (same-device, in this case)
The MATTR VII verifier tenant is configured with:
- The domains it can accept requests from
- The workflows it supports (e.g. same-device and/or cross-device)
- The supported protocols (e.g. Digital Credentials API and/or OID4VP)
- The wallet applications it can interact with
- How to invoke these wallet applications on the same device
Based on this configuration, the MATTR VII verifier tenant identifies that the user is using a mobile browser and returns a universal link or custom URI that can invoke the wallet app.
The Verifier Web SDK uses this link to redirect the user to their wallet application.
Presenting request details to the user
Once the wallet is launched, it authenticates the user and retrieves the verification request from the MATTR VII verifier tenant. The user is shown:
- The credentials being requested
- The claims required from those credentials
- Whether the relying party is trusted and authorized by the Digital Trust Service
- Which of the user’s credentials match the request
The user can then review and consent to sharing the information.
Verifying the credential
The MATTR VII verifier tenant verifies the presentation by checking:
- That the credential has not been tampered with
- That it has not been revoked or suspended
- That it has not expired
- That it was issued by a trusted issuer, validated via the configured Digital Trust Service
Displaying verification results
After the verification is complete, the wallet app redirects the user back to their mobile browser, returning them to the original web application using the previously provided redirect URl.
The Verifier Web SDK receives the verification result and renders it in the browser, allowing the user to view the outcome and continue their interaction.
The issuer of the credential is not informed that the presentation has occurred. No data about the verifier, the context of use, or the interaction itself is shared with the issuer. The only interaction with the issuer is a potential call to an online revocation endpoint, if revocation checking is required.
The MATTR VII verifier tenant can also be configured to return the verification result to a secure back-end service instead of the front-end, depending on implementation needs.
Journey flow - Cross-device

Accessing the service
Samantha opens a web application in a browser on her laptop. She begins an interaction that requires identity verification.
Architecture - Cross-device

Interacting with the website
The user accesses a website using a web browser on their desktop.
Requesting a credential for verification
On the website, the user begins an interaction that requires them to present a credential.
The MATTR Pi Verifier Web SDK, embedded in the web application, initiates the verification request by sending it to a configured MATTR VII verifier tenant. This request defines:
- The credentials and claims required
- The supported interaction modes (same-device, in this case)
The MATTR VII verifier tenant is configured with:
- The domains it can accept requests from
- The workflows it supports (e.g. same-device and/or cross-device)
- The supported protocols (e.g. Digital Credentials API and/or OID4VP)
- The wallet applications it can interact with
- How to invoke these wallet applications on the same device
Based on this configuration, the MATTR VII verifier tenant returns a link. The Verifier Web SDK recognizes Samantha is using a desktop browser and renders this link as a QR code on the webpage.
The user scans the QR code using a mobile device that has a compatible digital wallet installed. This action invokes the wallet app with the verification request.
Presenting request details to the user
Once the wallet is launched, it authenticates the user and retrieves the verification request from the MATTR VII verifier tenant. The user is shown:
- The credentials being requested
- The claims required from those credentials
- Whether the relying party is trusted and authorized by the Digital Trust Service
- Which of the user’s credentials match the request
The user can then review and consent to sharing the information.
Verifying the credential
The MATTR VII verifier tenant verifies the presentation by checking:
- That the credential has not been tampered with
- That it has not been revoked or suspended
- That it has not expired
- That it was issued by a trusted issuer, validated via the configured Digital Trust Service
Displaying verification results
The MATTR VII verifier tenant shares the verification results with the Verifier Web SDK. These results are displayed to the user in the browser, allowing them to continue their interaction
The issuer of the credential is not informed that the presentation has occurred. No data about the verifier, the context of use, or the interaction itself is shared with the issuer. The only interaction with the issuer is a potential call to an online revocation endpoint, if revocation checking is required.
The MATTR VII verifier tenant can also be configured to return the verification result to a secure back-end service instead of the front-end, depending on implementation needs.
How would you rate this page?
Last updated on

