Verify a selective-disclosure credential
MATTR VII supports selective-disclosure credentials, which give holders a privacy-preserving way of selectively disclosing limited sets of their data contained within credentials. In many jurisdictions, it is important to request only information that is required for legitimate purposes. GDPR, for example, legislates against over-collection of personal information. Setting up a presentation template with a QueryByFrame query method can help ensure that you comply with these requirements.
This tutorial will allow you to perform a credential Verify flow and obtain only the claim information from a selective-disclosure credential that has been requested, in addition to the Subject Identifiers and whether the credential has been fully verified or not.
Prerequisites
You need access to the MATTR Platform APIs. If you're experiencing any difficulties, contact us.
In order to complete this tutorial you will need the following:
A local development environment or remote service setup to accept
json/applicationCallbacksA known decentralised identifier (DID) to be used for messaging (i.e. a DID using
keyTypeofEd25519)The
idof aQuerybyFramepresentation request template configured on your tenant.A selective-disclosure enabled credential issued to the mobile wallet that can be matched the using the presentation request (i.e. matching
typeandissuerand associated claims).
Setup the sample app
We will use the verify credentials using presentation request callbacks sample app that will step you through creating a simple Node.js Express server to orchestrate many of the steps below.
Create your environment variables in an .env file and save it to the folder (rename the existing .env-template file).
TENANT=YOUR_TENANT_URL
TEMPLATEID=<presentation-request-template-uuid>
VERIFIERDID=<verifier-did>
TENANT: Use your tenant's URL.TEMPLATEID: Use theidof the presentation request template.VERIFIERDID: Use the verifier DID associated with your tenant.
Start the server
Append your valid MATTR VII access token to the end of the start command to start the Express server:
1npm start <access_token>The access token is stored in local memory and used to make API calls to your tenant over HTTPS
Once you run the server you should see a QR code in your terminal:

Scan the QR code using the mobile wallet app
Once the mobile app matches a credential to the presentation request, it will display the claims that have been requested and highlight all the claims that are not going to be disclosed to the verifier. This is an example of a large credential with limited claims being shared:
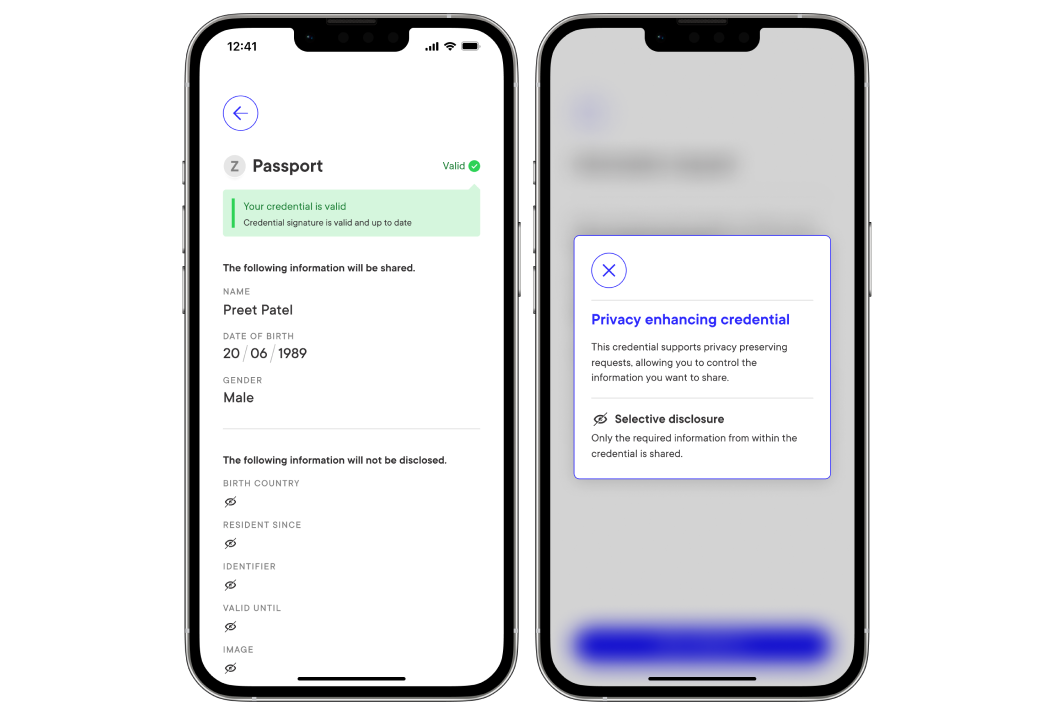
Receiving the credential presentation callback
Once a valid presentation is sent by the mobile app, MATTR VII performs some checks to ensure the validity of the presentation:
Issuer DID of each credential can be resolved.
JSON-LD context is valid for subject claims.
Proof is valid & the credential has not been tampered with.
Check any credential against its RevocationList2020 status (where applicable).
These checks will inform the verified boolean and where the content is mapped to fields and presented to the callback URL as an application/json body:
Callback URL Response
1{
2 "presentationType": "QueryByFrame",
3 "challengeId": "GW8FGpP6jhFrl37yQZIM6w",
4 "claims": {
5 "id": "did:key:z6MkfxQU7dy8eKxyHpG267FV23agZQu9zmokd8BprepfHALi",
6 "http://schema.org/familyName": "Shin",
7 "http://schema.org/educationalCredentialAwarded": "Certificate Name"
8 },
9 "verified": true,
10 "holder": "did:key:z6MkgmEkNM32vyFeMXcQA7AfQDznu47qHCZpy2AYH2Dtdu1d"
11 }